Most people think that microservices and SOA are the same concept. If you read the definition, you too will feel the same but it’s not really true. if we start from the beginning when the two concepts emerged, we realize that there was a significant time gap between them. The concept of Service oriented architecture or SOA emerged about a decade back while the concept of microservices started getting accepted around late 2013. It is only now that the latteris gaining some momentum. As is commonly seen in the IT industry, there are certain popular trends at any point in time which do not become popular overnight but have a steady upward climb over time. After sometime, when their popularity declines, they are revisited and presented with a new outlook.
Download Whitepaper: Test Data Management – Key Challenges and Test Approach
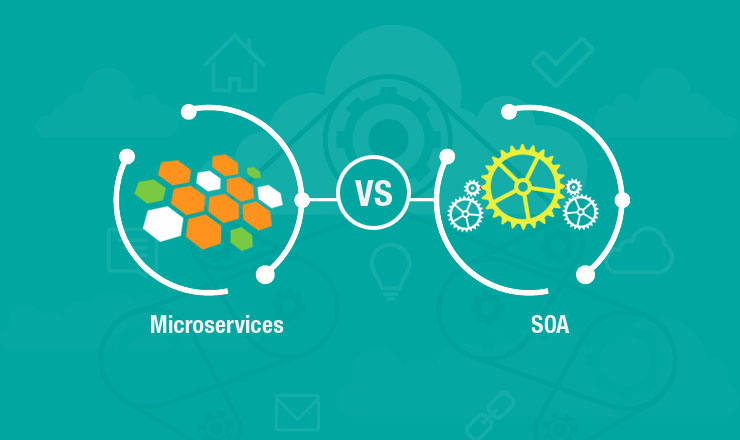
Understanding the difference between Microservices and Service oriented architecture
It important to reiterate that Microservices and Service Oriented Architecture are not the same though the basic idea for both stems from similar problems that are faced with complex applications. According to Martin Fowler, ‘SOA is a subset of Microservices’. For some other peopleMicroservices is about doing SOA the right way. Well, let me confess – there are many similarities in the two process like the concept of services being the cornerstone for architecture or how the services need to be independent of technology etc.
The difference between the two is in the very term ‘micro’. The focus is on smaller services in case of Microservices. The process breaks down a big application into smaller components and ensures that each of them has autonomy. Also they allow low coupling and high cohesion. This translates into the ability of the services to function independently of each other with an increased ability to add value to itself.
Another way to differentiate between the two processes is that the service in Microservices are significantly smaller than those in SOA though they are equally capable as standalone services. SOA on the other hand covers the entire system and may bring about changes in the way IT is handled in the organization. It essentially has a larger scope of influence.
What sets them apart?
There are three perceptible differences between SOA and Microservices. These are based on how the two concepts are used. These are:
- It is unlikely that in an SOA environment, there will be a place for Microservices. In that sense, as far as application is concerned, both are mutually exclusive.
- Microservices architecture and heavy application servers do not get together so it is unlikely that both will function together.
- The concept of automation whether in infrastructure or in other processes is a significant part of deployment of Microservices architecture.
One thing that is challenging about microservices is their testing. The testing complexities can be rooted out by testing each component in a layered manner. With this, the system can be tested at each level resulting in a better test coverage. The following measures should be taken out to eliminate the testing complexities as a whole.
- Each component ought to be tested individually by the independent teams working on different parts of microservices.
- Properly handle the responses received by the multiple consumers of microservices.
- All the services within microservices are inter-related and inter-dependent. Changes in any of them can bring about the alterations in the functions of others.
Download Whitepaper: Testing for Internet Of Things (IoT) – How is it different?
Conclusion
Both Microservices and SOA are focused on solving different issues. While the former is the way in which smaller applications are structured in a bigger and more complex environment, SOA can be seen as a strategic approach to problem solving. It is about bringing a change in the structure of the entire enterprise by separating them into different services and thus making them more flexible.
Other Resources